Jean-Philippe Aumasson
Principal cryptographer at Kudelski Security
Jean-Philippe (JP) Aumasson is a cryptographer, author of the books Serious Cryptography (No Starch Press, 2017) and The Hash Function BLAKE (Springer, 2015), and designer of the BLAKE2 and SipHash algorithms. JP works as an independent
consultant, while holding a 30% part-time position at Kudelski Security and a position of Lead Security Advisor for a Swiss fintech start-up. He has spoken at Black Hat, DEFCON, RSA, CCC+SyScan, Troopers about applied cryptography,
quantum computing, and platform security. He likes finding bugs in cryptocurrency and blockchain technologies, and even gets paid for it.
Zoz
Hacker, robotics expert and educational media personality
Zoz is a hacker, robotics expert and educational media personality whose interests center on the interactions between humans and technology in the form of human-machine interfaces, design, and individual empowerment. He has taught
subjects including robotics, digital fabrication, cybersecurity and ethical hacking at top international universities and as a private industry consultant. He has hosted and appeared on numerous international television shows including
Prototype This!, Time Warp and RoboNationTV. He speaks frequently at prominent security and hacking conferences including DEF CON, HackCon and BruCon, volunteers as the MC for BSides Las Vegas and on the review committee for DEF CON,
and is a 2-time DEF CON black badge winner. He believes warranties exist to be voided.
Lecture #1: Hacking driverless cars:
A presentation from DEFCON a few years ago, updated with new research made since then, plus an overview of the DOT's plans for V2V (vehicle-to-vehicle) and V2I (vehicle-to-infrastructure) wireless communications. These vehicles will eventually
be part of the IoT, but they are not yet.
Lecture #2: Rapid prototyping tools and techniques
A lecture on rapid prototyping tools and techniques, like laser cutting and 3D printing, including DIY hacks for electronics fabrication and assembly.
Workshop #1: A Robot Operating System (ROS) tutorial
You need to follow this tutorial to be able to follow this workshop!
A tutorial for getting started with the Robot Operating System (ROS) using the Gazebo simulator. Robots are not common IoT devices yet, but they will be eventually, and there's a good chance if you encounter one in the wild it could be running
ROS. (Some industrial robots like Rethink's Baxter and Sawyer already do.) The tutorial is an intro level tut, presented in a hacking context, like sending spoofed GPS information, malicious command injection, DOSing ROS nodes and
so on.
Workshop #2: CTF challenges
A few entry-level CTF challenges that the students can take a shot at. They were developed for college-age students just getting in to infosec and hacking. Some of these will be added to the official CTF.
Andrea Barisani
Founder at Inverse Path, Head of Hardware Security at F-Secure
Andrea Barisani is an internationally recognized security researcher, founder of security consultancy Inverse Path, now part of F-Secure where he assumed the role of Head of Hardware Security. Since owning his first Commodore-64
he has never stopped studying new technologies, developing unconventional attack vectors and exploring what makes things tick...and break. His experiences focus on large-scale infrastructure defense, penetration testing and code auditing
with particular focus on safety critical environments, with more than 15 years of professional experience in security consulting. Being an active member of the international open source and security community he contributed to several
projects, books and open standards. He is a well known international speaker, having presented at BlackHat, CanSecWest, Chaos Communication Congress, DEFCON, Hack In The Box, among many other conferences, speaking about innovative
research on automotive hacking, side-channel attacks, payment systems, embedded system security and many other topics.
Lecture #1 (60 minutes): Real-life experiences in avionics security assessment:
The lecture aims to provide insights on real-life experiences gathered from the security assessment of modern avionics systems. Particular focus is placed on explaining how the interaction between safety and security is
assessed and how responsible teams can interact and to combine their diverse set of skills. An example technical overview of the classes of systems, interfaces and audit methodologies is given to precisely demonstrate how work in this
area is laid out and executed, and to emphasize its importance in the transportation industry. Finally the unique culture of safety in modern aviation is compared to similar safety-critical areas, such as the automotive field, to highlight
the differences and similarities.
Lecture #2 (120 minutes): Trusted Execution Environments with modern SoCs:
The availability of modern System on a Chip (SoC) parts, having low power consumption and high integration of most computer components in a single chip, empowers manufacturers in in creating secure embedded systems. The lecture explores the
common security features found in typical SoC configurations, such as secure boot and cryptographic co-processors, and how they can be leveraged to achieve trusted execution environments of all kind. We will explore state of the art
techniques to take advantage of SoC security features as well as potential mistakes and vulnerabilities. Finally an in depth overview of ARM TrustZone will highlight its strength and weaknesses.
Vlatko Košturjak
CTO at Diverto, Croatia
Vlatko Kosturjak is CTO at Diverto where he helps clients to reach desired security level(s). He likes to break and build depending on the mood and time of day(night). Beside security, his passion is open and free software, so
he authored open source security tools which are used in CTFs and pentests worldwide. He also contributed code to various free security software like OpenVAS, Nmap and Metasploit.
Lecture #1: MIPS and ARM exploitation
Tim Panton
CTO at |pipe|, UK
Tim Panton (@Steely_glint) is a software developer with an infosec history. He loves learning new things. He is currently busy as CTO at |pipe| building a secure, easy to use distributed transport and identity layer for the internet
of things. He is a recovering open source VoIP coder.
The CTF Challenge
Every team that competes in the CTF will be given a drone that they need to secure/harden as much as possible. The teams will then get a task that their drones need to accomplish, while getting attacked by the other
teams. After the first round, the teams will then again have some time to make improvements to their drone, after which they try to finish te task one last time. The reward pool for the CTF is currently 1 ETH, sponsored by Bitfalls.
Nicolas Bodin
Researcher and lecturer at ESIEA
Nicolas Bodin obtained his PhD in 2013 following a thesis in steganography. He has since been a researcher teacher in a french engineering school, the ESIEA.
He teaches C programming for undergraduate students and is particularly interested in new teaching methods. His favorite research topics are steganography and steganalysis although he is not afraid to write articles when he finds some
nice properties in relation to Venn diagrams with his colleague Arnaud Bannier.
Arnaud Bannier
Researcher and lecturer at ESIEA
Arnaud Bannier is a lecturer and researcher at (C+V)^O research lab at the french engineering school ESIEA. He holds a PhD in cryptography and is co-author of the book Partition-based Trapdoor Ciphers (InTech editions, 2017).
He teaches C programming, algebra and cryptography. His research topics are of course Cryptography and Cryptanalysis, even if he might work in Steganography with his colleague Nicolas Bodin in the future.
Steganography challenge: a two-part lecture (each part 180 minutes):
Lecturers: Nicolas Bodin and Arnaud Bannier
Steganography is a way to hide a communication into another innocuous one. During these lectures, you will discover some ways to practice and
detect steganography in digital media such as images, web pages, executable files... These lectures are organized in several independant challenges, each starting with a short tutorial.
Kirils Solovjovs
Lead Researcher at Possible Security
Mg. sc. comp. Kirils Solovjovs is a Lead Researcher at Possible Security and the most visible white-hat hacker in Latvia. He has extensive experience in network flow analysis, reverse engineering, social engineering and penetration
testing. He has discovered and responsibly disclosed or reported multiple security vulnerabilities in information systems of both national and international significance, as well as IoT devices.
Lecture #1 (180 minutes): RFID attacks and Proxmark hands-on
Lecture #2 (180 minutes): Live network forensics and reversing network protocols
Goran Hacek
CEO at Occam, Croatia
Goran is a software engineer by education, but with his 31 years of age has spent half of his life in IT and has gathered experience on various projects in different industries. Recently he started his own company where he and
his team help their clients convert ideas into successful products. They specialize in IoT and connected devices, where they build the whole stack, from custom hardware to all software needed to run the devices and the network.
Workshop #1 (180 minutes): An intro to IoT /w Arduino
A hands-on workshop about the basics of Arduino programming and a bit of hardware basics. How to read and write analog/digital stuff. Controlling a LED, reading a light sensor. Sending the sensor data to a server.
Workshop #2 (180 minutes): IoT for WebDevs
A hands-on workshop about hardware basics, without any hardware programming. The students get an Arduino kit with a preinstalled WebSockets server, which they control and get status info using JavaScript. Prior JavaScript
knowledge is required for this workshop.
Luka Perkov
Managing Director at Sartura, Croatia
Luka Perkov has been working with embedded Linux systems for over a decade. He initiated and now manages several FOSS projects whose goal was to fill the gap between the industry requirements and available community software. Luka officially became an OpenWrt developer in 2011. One of his first full time employers was a medium-sized Internet Service Provider, where he worked as an Administrator for Broadband Solutions. He left this position and founded a software company, Sartura, with strong focus on embedded development. Today he is managing the company. Luka obtained his master's in computing science at the Faculty of Electrical Engineering and Computing, Zagreb, Croatia. Soon after he enrolled in a specialist postgraduate study Information Security at the same university. He gained his academic title, specialist in information security, after defending thesis "Security issues with remote configuration of internet service providers' network equipment" in 2014.
Lecture (45 minutes): ISP's black box
Marin Bek
CEO at Kraken and Ascalia
Marin Bek started out as a robotics engineer, creating his first company in Palo Alto in 2011 building autonomous underwater “drones”. Since then, he moved on to be the CTO at Nextuser in San Francisco, helping in getting 2.5M$ in funding and growing the tech team to more than 25 people, working with clients like Ferrero, Nestle, Carrefour…
He is currently the founder and CEO of Kraken d.o.o. (KrakenSystems) in Zagreb, helping companies scale and solidify their products, mainly in the area of large, distributed systems. He is constantly looking for new challenges and building new companies. When he’s not working, you can find him rock-climbing in the nearest crag.
Dejan Strbad
CTO at Kraken and Ascalia
Dejan is the CTO in KrakenSystems, with over 10 years of professional experience in a wide range of software development, SRE, Ops and systems architect roles. He is the main figure in supporting Nextuser’s distributed high-load system spreading over 4 continents and helping their other clients tackle their technical challenges. Lately his focus is on building Ascalia, ICS for 21st century... He is constantly looking for new challenges, building new companies and likes to exchange knowledge through meetups, workshops and conferences. In his free time, he is involved in political activism through civil society initiatives.
Lecture (45 minutes): Industrial Control Systems
Lecturers: Marin Bek and Dejan Strbad
An overview of available solutions, pros and cons. What's next in the era of IoT?
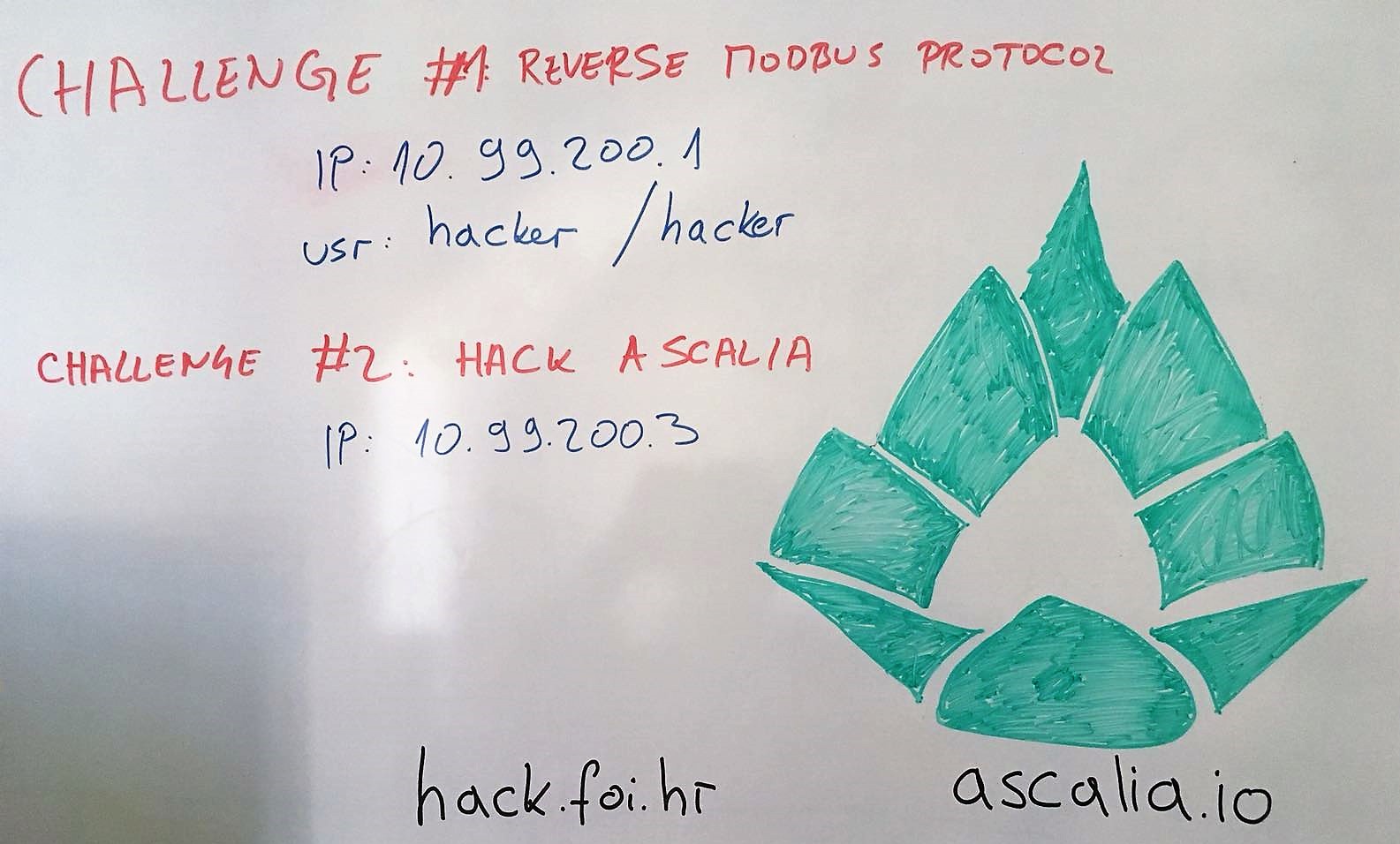
Workshop (3 hours): Hacking session of Industrial Control Systems
Lecturers: Marin Bek and Dejan Strbad
The challenges are listed below. You'll need to be connected to our FSEC_HACK2018 network in order to access the IPs.
Boris Tomaš
Senior Teaching Assistant/Postdoctoral Researcher at Faculty of Organization and Informatics, University of Zagreb
Lecture (1 hour): Visible Light Communication in Vehicular Networks
VLC is a novel communication technology which uses a terahertz-wide, unlicensed visible light spectrum. It has a great potential in supplementing or even replacing the existing radio frequency (RF) communication technologies in application as diverse as device-to-device
(D2D) communications, vehicle-to-vehicle (V2V) communications, vehicle-to-infrastructure and infrastructure-to-vehicle communication, and small-cell (e.g., femtocell) systems. The physical characteristics are similar to infra-red (IR) communication; similar to IR, VLC also
uses the spectrum that is under atmospheric window effect, thus making it highly sensitive to solar radiation noise. In vehicular communication setting, VLC is particularly interesting, since most of the components that are needed to enable VLC are already
part of a modern vehicle. Specifically, an LED, LASER, or any other light emitting technologies that can be controlled using micro controllers and can be used as a VLC transmitter (Tx). Conveniently, headlights and taillights of modern vehicles contain LED lights, with
LASER lights being envisioned in the near future. Similarly, VLC receiver (Rx) component is usually either a photodiode (PD) or a CMOS camera, which can be found in many modern vehicles (e.g., a front camera for lane tracking or a rear camera for parking assistance).
Hetti - Petar Kosić
Technical computer science student from Vienna with a passion for IT Security and geeky stuff. - Metalab, Vienna
He is one of the board members of the finest Viennese Hackspace Metalab. In his free time he enjoys travelling to community based IT Conferences.
The Viennese Cryptoparty is organized by him, where he also holds lectures and workshops about a broad range of IT Security & Privacy topics.
You can also find him at the Chaos Computer Club Vienna (C3W). On some weekends he is hunting flags with the successful academic CTF Team We_0wn_Y0u.
Lecture (1 hour): Security Safari in b0rkenLand - Watch out! There are dangerous security problems out there.
Check out the slides here!
A small travel from broken metal chunks to "undocumented user accounts" and other security holes.
IT respectively computer security is an interesting area. Not only for criminals but also for scientists, programmers and users. We all should know that 100% security does not exist.
Therefore I would like to underpin this statement with this lecture.
I will present a selection of security holes/problems that appeared during 2018 and will give you an insight into that part of the IT security world.
You will probably see your software and hardware differently after this lecture
Tonimir Kišasondi
Head of Open Systems and Security Laboratory at Faculty of Organization and Informatics, University of Zagreb
Tonimir Kišasondi is the Head of the Open Systems and Security Laboratory at the Faculty of Organization and Informatics where he mentors students in the art of information security. From his industrial cooperation side, he specializes
in helping software, IoT and blockchain companies from the EU and US build secure products from the design to the production stage. His professional and research area of interest is security architecture, security testing & analysis
and applied cryptography.